oc apply -f bootstrap-acm-global-gitops/setup.yaml
ACM & ArgoCD for Teams
Tags : openshift, argocd, acm, gitops
Quickly deploying ArgoCD ApplicationSets using RHACM’s Global ClusterSet
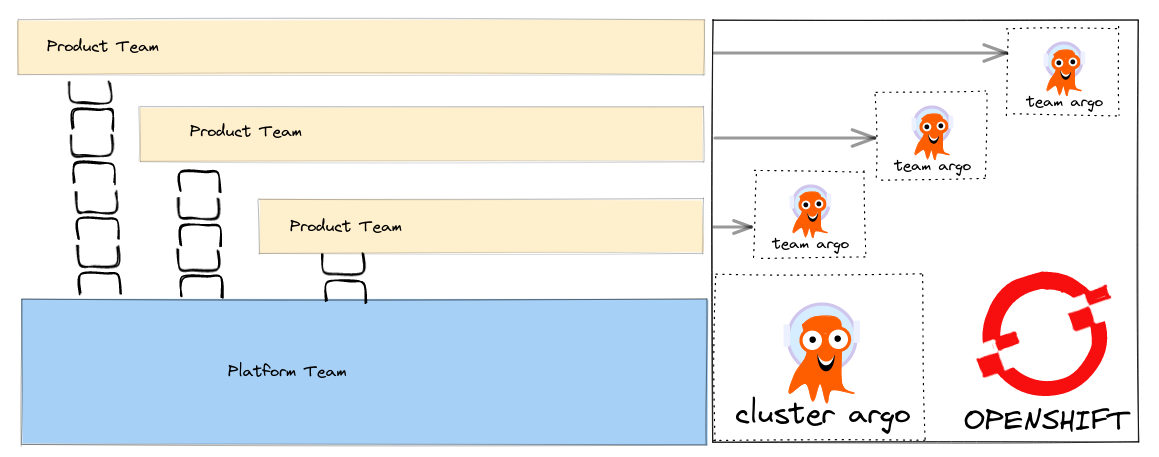
I have written about how we can align our Tech to setup GitOps tooling so that it fits with our team structure.
How can we make these patterns real using tools like Advanced Cluster Manager (ACM) that help us deploy to a fleet of Clusters ? ACM supports Policy based deployments so we can track compliance of our clusters to the expected configuration management policy.
The source code is here - https://github.com/eformat/acm-gitops - git clone it so you can follow along.
Global ClusterSet’s
When a cluster is managed in ACM there are several resources created out of the box you can read about them here in the documentation. This includes a namespace called open-cluster-management-global-set. We can quickly deploy ApplicationSet’s in this global-namespace that generates Policy to create our team based ArgoCD instances.
We can leverage the fact that ApplicationSet’s can be associated with a Placement - that way we can easily control where our Policy and Team ArgoCD’s are deployed across our fleet of OpenShift clusters by using simple label selectors for example.
Bootstrap a Cluster Scoped ArgoCD for our Policies
We are going Bootstrap a cluster-scoped ArgoCD instance into the open-cluster-management-global-set namespace.
We will deploy our Team ArgoCD’s using ACM Policy that is generated using the PolicyGenerator tool which you can read about here from its' reference file.
Make sure to label the cluster’s where you want to deploy to with useglobal=true.
This deploys the following resources:
-
SubscriptionResource - The GitOps operatorSubscription, including disabling the default ArgoCD and setting cluster-scoped connections for our namespaces - see theARGOCD_CLUSTER_CONFIG_NAMESPACESenv.var that is part of theSubscriptionobject. If your namespace is not added here, you will get namespace scoped connections for your ArgoCD, rather than all namespaces. -
GitOpsClusterResource - This resource provides a Connection between ArgoCD-Server and the Placement (where to deploy exactly the Application). -
PlacementResource - We use aPlacementresource for this global ArgoCD which deploys to a fleet of Clusters, where the Clusters needs to be labeled withuseglobal=true. -
ArgoCDResource - The CR for our global ArgoCD where we will deploy Policy. We configure ArgoCD to download thePolicyGeneratorbinary, and configure kustomize to run with the setting:
kustomizeBuildOptions: --enable-alpha-pluginsDeploy the Team Based ArgoCD using Generated Policy
We are going to deploy ArgoCD for two teams now using the ACM PolicyGenerator.
The PolicyGenerator runs using kustomize. We specify the generator-input/ folder - that holds our YAML manifests for each ArgoCD - in this case one for fteam, one for zteam.
You can run the PolicyGenerator from the CLI to test it out before deploying - download it using the instructions here e.g.
kustomize build --enable-alpha-plugins team-gitops-policy/We specify the placement rule placement-team-argo - where the Clusters needs to be labeled with teamargo=true.
We add some default compliance and control labels for grouping purposes in ACM Governance.
We also set the pruneObjectBehavior: "DeleteAll so that if we delete the ApplicationSet the generated Policy s deleted and all objects are removed. For this to work, we must also set the remediationAction to enforce for our Policies.
One last configuration is to set the ArgoCD IgnoreExtraneous compare option - as Policy is generated we do not want ArgoCD to be out of sync for these objects.
apiVersion: policy.open-cluster-management.io/v1
kind: PolicyGenerator
metadata:
name: argocd-teams
placementBindingDefaults:
name: argocd-teams
policyDefaults:
placement:
placementName: placement-team-argo
categories:
- CM Configuration Management
complianceType: "musthave"
controls:
- CM-2 Baseline Configuration
consolidateManifests: false
disabled: false
namespace: open-cluster-management-global-set
pruneObjectBehavior: "DeleteAll"
remediationAction: enforce
severity: medium
standards:
- generic
policyAnnotations: {"argocd.argoproj.io/compare-options": "IgnoreExtraneous"}
policies:
- name: team-gitops
manifests:
- path: generator-input/Make sure to label the cluster’s where you want to deploy to with teamargo=true.
To create our Team ArgoCD’s run:
oc apply -f applicationsets/team-argo-appset.yamlTo delete them, remove the AppSet
oc delete appset team-argoSummary
You can now take this pattern and deploy it across multiple clusters that are managed by ACM. You can easily scale out the number of Team Based ArgoCD and have fine grained control over their individual configuration including third party plugins like Vault. ACM offers a single plane of glass to check if your clusters are compliant to the generated policies, and if not - take remedial action.
You can see the code in action in this video.
🏅Enjoy !!
